Volt Typhoon's Lasting Impact
March 3, 2024 | Expert Insights

The already strained relationship between the United States and China has taken another hit with the discovery of the Volt Typhoon, a Chinese state-sponsored hacking group, residing undetected within crucial US infrastructure for an estimated five years. This revelation has triggered significant alarm, raising concerns about potential disruptions and the weaponization of critical infrastructure during future international conflicts.
Background
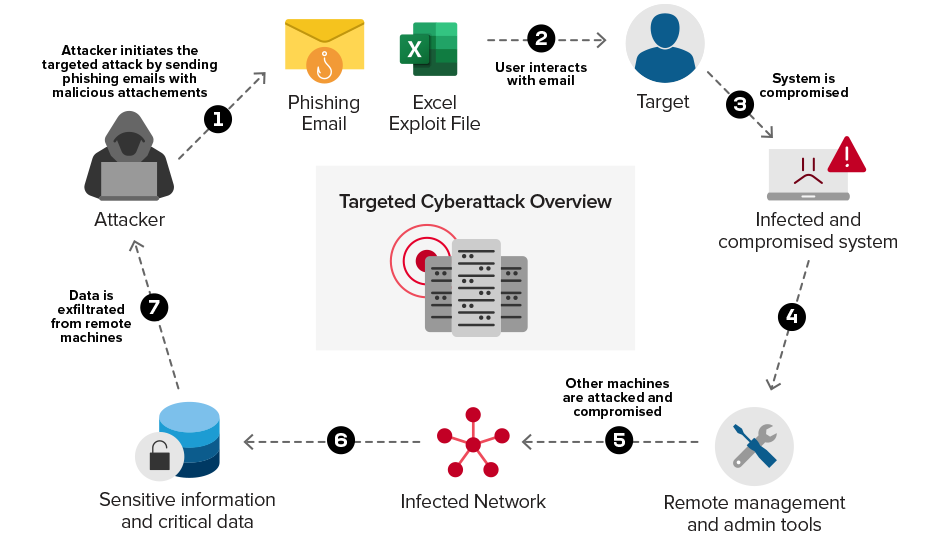
Volt Typhoon, a state-sponsored hacking group, employs a concerning strategy that deviates from conventional methods. They exploit readily available vulnerabilities in outdated and poorly maintained systems, such as end-of-life routers, firewalls, and virtual private networks (VPNs). These systems, prevalent in many organizations due to inadequate maintenance and infrequent security updates, offer easy access points for attackers. Further enhancing their stealth, Volt Typhoon utilizes "living off the land" techniques. This approach involves manipulating legitimate tools and resources already present within the targeted system, rather than introducing new and easily identifiable malware. By seamlessly blending their activities with regular system operations, they significantly hinder detection efforts by making it difficult to distinguish malicious activity from normal system functions.
This unique and concerning approach highlights the importance of prioritizing robust cybersecurity measures, particularly within critical infrastructure. Upgrading outdated systems, implementing strong security protocols, and fostering a culture of cyber hygiene within organizations are crucial steps toward mitigating the risks posed by sophisticated threat actors like the typhoon.
Analysis
US authorities have revealed that the Volt Typhoon's unusual targeting choices and behavioural patterns deviate from conventional cyber espionage or intelligence-gathering operations. Since mid-2021, their activities have been documented, with Microsoft’s investigations suggesting their focus on "pursuing the development of capabilities that could disrupt critical communications infrastructure between the United States and Asia region during future crises." A joint report by the Cybersecurity and Infrastructure Security Agency (CISA), the National Security Agency (NSA), and the Federal Bureau of Investigation (FBI) concluded that "People's Republic of China (PRC) state-sponsored cyber actors are seeking to pre-position themselves on IT networks for disruptive or destructive cyberattacks against US critical infrastructure in the event of a major crisis or conflict with the United States."
Beijing consistently denies accusations of cyberattacks and espionage linked to or backed by the Chinese state. However, evidence of their cyber-espionage campaigns has been mounting for over two decades. While the US government and its allies attribute the recent intrusions to the Volt Typhoon, China dismisses these claims, labelling them "baseless attacks and smears."
The extensive nature of the hacks prompted a series of meetings between the White House and private technology companies, seeking assistance in tracking the activity. CISA mandated institutions and assets targeted by the dismantled botnet to disconnect affected devices and products, initiating a complex and challenging remediation process. Security researchers categorize the Volt Typhoon as a top-tier cybergang, highlighting the seriousness of the threat.
The discovery of Volt Typhoon and its ability to remain undetected for extended periods has solidified its position as a top-tier cybergang, according to security researchers. This designation underscores the significant threat posed by the group, particularly their suspected capability of developing zero-day exploits – vulnerabilities previously unknown to security experts. These exploits enable attackers to bypass existing security measures, significantly increasing the potential for successful cyberattacks.
Furthermore, the discovery of the Volt Typhoon has exacerbated the already strained relationship between the United States and China. While China continues to deny any involvement in state-sponsored cyberattacks and espionage, the US government and its allies firmly attribute the recent intrusions to the group, labelling them a state-sponsored threat actor. This discrepancy in narratives further complicates the already tense diplomatic environment, highlighting the need for clear communication and international cooperation to address evolving cybersecurity threats. The situation surrounding the Volt Typhoon underscores the importance of robust cybersecurity measures on both national and international levels. Additionally, fostering a spirit of collaboration and information sharing between nations is crucial in combating sophisticated cyber threats and safeguarding critical infrastructure from potential disruptions and attacks.
The discovery of the Volt Typhoon and its sophisticated tactics pose significant challenges beyond the immediate US-China relations. Firstly, it exposes the global vulnerability of critical infrastructure across various nations. This revelation serves as a stark reminder of the urgent need for countries to prioritize robust cybersecurity measures and invest in upgrading outdated systems. Outdated infrastructure with unaddressed vulnerabilities presents easy access points for malicious actors, potentially jeopardizing vital services such as energy grids, water treatment plants, and communication networks.
Secondly, the case of Volt Typhoon raises concerns about the potential weaponization of critical infrastructure. The group's suspected ability to disrupt essential services during international conflicts underscores the potential consequences of cyberattacks as instruments of international warfare. This emerging threat highlights the need for global discussions and international agreements to deter and mitigate such actions, ensuring responsible behaviour in cyberspace.
Finally, the complexities surrounding the Volt Typhoon necessitate international collaboration among governments, security agencies, and the private sector. This collaboration is crucial for developing a comprehensive response to combat sophisticated cyber threats and build resilience across the globe. Sharing intelligence, fostering information exchange, and developing joint cyber defence strategies are essential steps in this collective effort.
Assessment
- Combating the ever-evolving cyber threat landscape demands immediate action and long-term strategies. Addressing the vulnerabilities exploited by the Volt Typhoon necessitates a multi-pronged approach at national and international levels.
- Upgrading outdated equipment, implementing robust security protocols with strong authentication measures, and fostering a culture of cyber hygiene within organizations are crucial steps towards building a more secure environment.
- The discovery of Volt Typhoon serves as a wake-up call for the global community. By understanding the evolving threat landscape, prioritizing robust security practices, and fostering international cooperation, we can work towards a future where critical infrastructure remains secure and serves as a foundation for global prosperity, not a potential weapon in international conflicts.








Comments