Uber paid bounty to hacker
December 7, 2017 | Expert Insights

Uber reportedly paid $100,000 to the man responsible for its data breach. The money was transferred to ensure this 20-year-old man from Florida, USA, destroyed the data he breached in the first place.
Background
Uber Technologies Inc. is a global transportation technology company headquartered in San Francisco, California, United States, operating in 633 cities worldwide. It develops, markets and operates the Uber car transportation and food delivery mobile apps. Uber drivers use their own cars although drivers can rent a car to drive with Uber. The company was started in 2009.
Travis Kalanick was one of the co-founders and its former CEO. Considered to be one of the most successful companies in the world, Kalanick was forced to step down in June 2017 after an internal revolt by five of Uber’s largest investors. He remains on the company’s board. The board revolt occurred due to a series of controversies that have plagued the company in the recent year and a half. This includes claims by former employees about the working conditions within the company. A blog by a former employee Susan Fowler about the sexual harassment rampant at Uber went viral. This led to Uber firing more than 20 members of its staff and taking action against others following a review of more than 200 HR complaints that included harassment and bullying. The company has been repeatedly accused of harboring a “frat boy” culture within its walls.
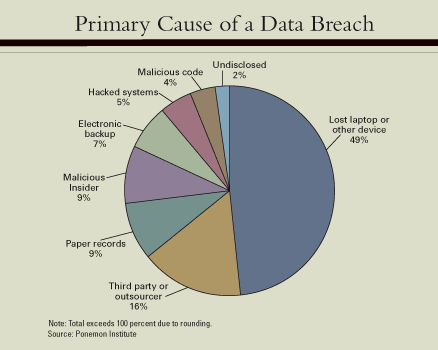
Analysis
According to confirmed media reports, ride-sharing technology company Uber, concealed a hack that affected 57 million customers and drivers. The hack took place in 2016 and then-CEO Travis Kalanick reportedly was privy to the fact. The paid hackers $100,000 to keep the massive breach a secret.
The hackers were able to get 57 million names, email addresses and mobile phone numbers. The names and driver’s license numbers of around 600,000 drivers in the United States were also compromised. Current CEO Khosrowshahi confirmed the breach in a statement adding, “I recently learned that in late 2016 we became aware that two individuals outside the company had inappropriately accessed user data stored on a third-party cloud-based service that we use. The incident did not breach our corporate systems or infrastructure. None of this should have happened, and I will not make excuses for it. While I can’t erase the past, I can commit on behalf of every Uber employee that we will learn from our mistakes. We are changing the way we do business, putting integrity at the core of every decision we make and working hard to earn the trust of our customers.”
Reuters has now reported that the company paid a 20-year-old man $100,000 from Florida to keep the breach a secret. The money was transferred to the man responsible for the breach in the first place. He was paid this money to destroy the data. The report noted, “Uber made the payment last year through a program designed to reward security researchers who report flaws in a company’s software, these people said. Uber’s bug bounty service - as such a program is known in the industry - is hosted by a company called HackerOne, which offers its platform to a number of tech companies.”
HackerOne CEO Marten Mickos said he could not discuss an individual customer’s programs. “In all cases when a bug bounty award is processed through HackerOne, we receive identifying information of the recipient in the form of an IRS W-9 or W-8BEN form before payment of the award can be made,” he said, referring to U.S. Internal Revenue Service forms.
The company has not provided any clarity over its decision to pay the bounty and to keep the breach a secret. Then CEO Kalanick had reportedly known about the bounty payment as well.
Assessment
Our assessment is that Uber’s actions and lack of transparency could erode the trust it shares with its customers and this could further damage the brand. This also shows just how vulnerable large organizations are to data breaches. It is imperative for governments and corporations to have processes in place that anticipate such attacks and have ready contingencies to tackle it.







Comments