Rampaging Digital Scourge
June 8, 2021 | Expert Insights

Early this month, a private fuel supplier in the U.S., Colonial Pipelines Corporation, came under a severe ransomware attack which forced the closure of its 5500miles gas pipeline that supplies almost 45% of the fuels to the American East Coast. Not surprisingly, it caused disruption, widespread panic, and a surge in prices. As per the Wall Street Journal, the CEO of Colonial, Joseph Blount, promptly paid a ransom of $4.4, unsure of the extent of the breach and how long it would take to regain control.
The fuel situation has been made precarious because in the search to cut operating costs, gas suppliers have over the years wound down more traditional forms of supplying fuel to consumers, like road and rail tankers etc., and have relied heavily on a single pipeline. It was a lucrative target by any measure, ripe for the picking. FBI laid the blame on DarkSide, a cyber-criminal gang based in Eastern Europe.
Elliptic, a blockchain analytics firm, claims from its research on bitcoin wallets that in the last nine months, DarkSide had made almost $90million from 47 of its ransomware targets. President Biden blamed the attack on Russia based cyber gangs, although he allowed Kremlin the benefit of the doubt, but asked President Putin to “take decisive action” against them. While the Colonial attack garnered all the attention, it was not the only ransomware attack. Toshiba, the Japanese megacorporation, also had its European operations attacked by DarkSide while Ireland’s health service too suffered a severe ransomware attack.
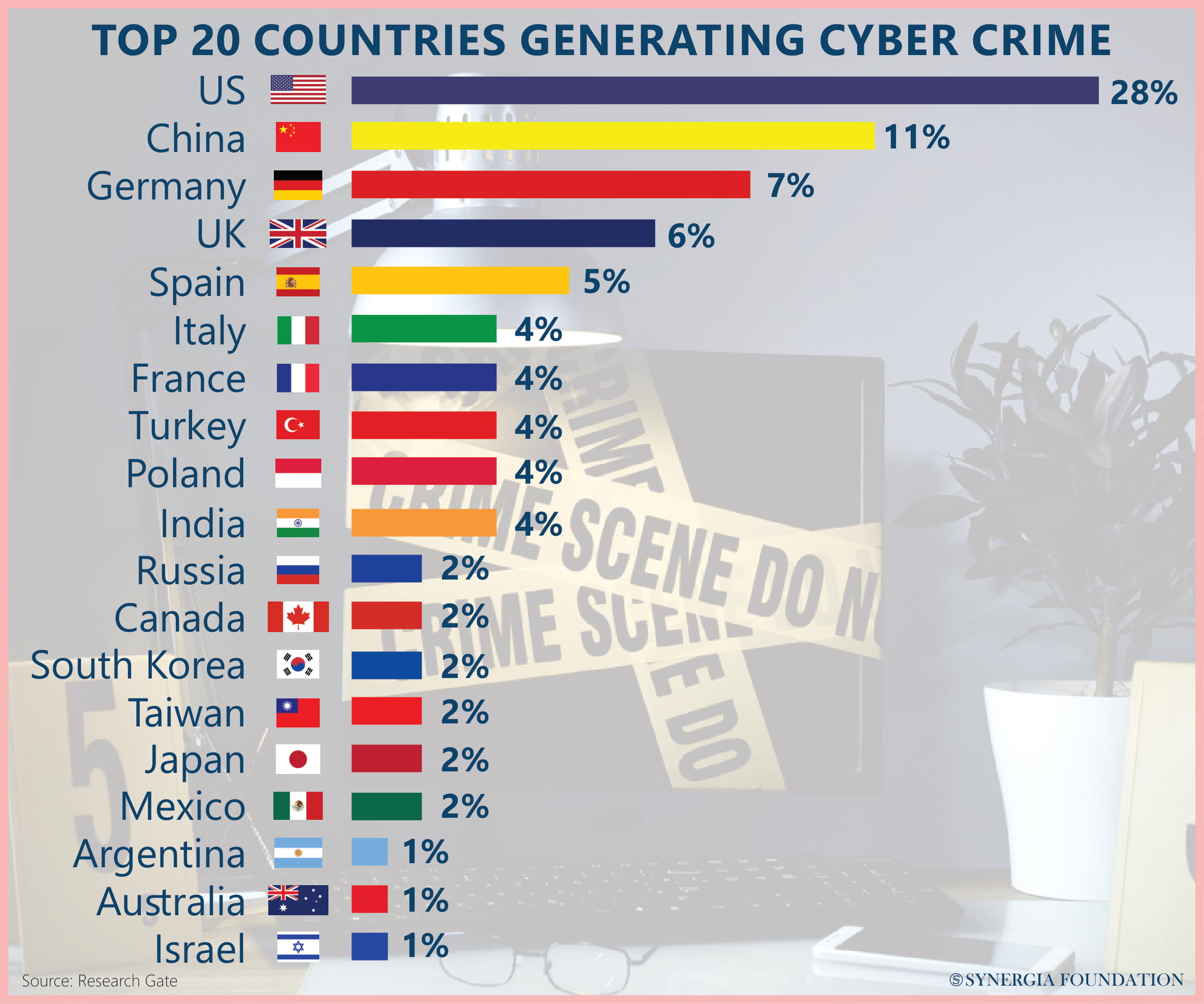
A GATHERING STORM
Ransomware attacks have been around for some time now, but their intensity has peaked in the last couple of years, facilitated by the widespread use of bitcoins which provide anonymity and speed in large online transactions. With more of the global infrastructure, both private and public becoming digitised, the targets have increased exponentially. Essentially a malware that, after breaching the system, encrypts and locks the files until a decryption code is supplied by the hacker on payment through bitcoins.
The underlining threat is not only denying access to critical data or deleting it but also making public millions of files of individuals containing sensitive information. Hackers are indiscriminate in the selection of their victims, picking from ordinary citizens to small businesses through phishing, watering-hole attacks and targeting larger wealthy corporations using sophisticated digital tools. In fact, skilled programmers and hackers with impressive portfolios offer readymade malware that can be easily downloaded from their Ransomware-as-a-service (RaaS) websites.
Thus, Ransomware in itself has become an economy of sorts, constantly improving and enhancing its software in accordance with ever- improving cybersecurity measures. The magnitude and the scope of the threat lie in the nature of cyberspace today that is not limited to just the IT/software sector or the world wide web. It facilitates global businesses, financial systems, communications flows, energy grids and various kinds of defence equipment through cloud computing and data analysis. An attack on such a sophisticated and interconnected cyber-realm can easily spill over and leave ramifications across sectors globally.
According to McAfee and the CSIS, 1 per cent of global GDP (almost $600 billion) is lost due to incessant cybercrimes and ransomware attacks. Cybersecurity Ventures predicts cybercrime will cost the world more than $6 trillion annually by 2021, up from $3 trillion in 2015. The report further adds that this represents the greatest transfer of economic wealth in history and that cybercrime risks the incentives for innovation and investment.
Of even greater concern is the threat such attacks pose to the health care sector. From the time digitisation of personal health info (PHI) started, health facilities and pharmaceutical companies have been the biggest target for malicious ransomware hackers. The British National Health Service was crippled when 40 of its hospitals lost patient appointments, critical surgery schedules and even re-routing of ambulance services in one of the biggest ransomware attacks. India reportedly saw an increase of 31 per cent in ransomware attacks in the pandemic, most of which targeted healthcare and associated industries.
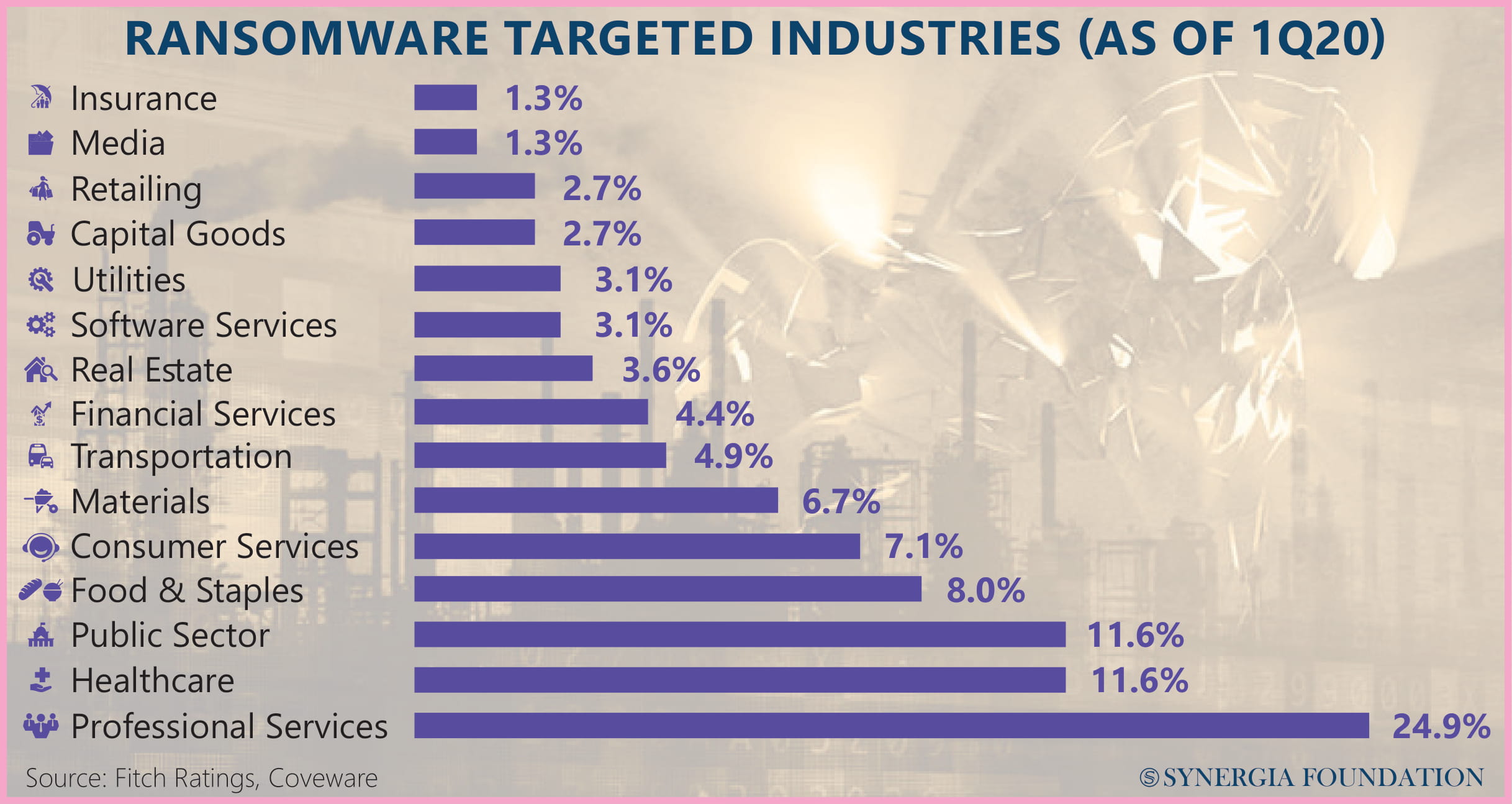
The threat to national security was amply demonstrated in 2017 when WannaCry, a ransomware worm, employed the hacking tools developed by the U.S. National Security Agency (NSA) to target a weak patch within the Microsoft Windows system. This then allowed the malware to enter the system and exploit the stored data. It affected almost 2 lakh computer systems across 150 countries, creating widespread loss, confusion, and disruption.
A HOUSE DIVIDED
A curious divide is clearly at play in the international community’s efforts to mount a counteroffensive.
The western nations spearheaded by the U.S. insist upon minimal government role and control of what should ideally be a free, safe, and secure cyber-realm. They promote a multi-stakeholder approach where key stakeholders come together to participate in deliberation, decision making and implementation of laws and policies and thus take collective responsibility.
Other nation-states led by Russia and China put forward the sovereignty of the state above everything else and a non-interference of cyberspace in the state’s political affairs. It is a more authoritarian approach that insists on state control over digital networks. This fundamental divide plays out while drafting international laws and standards on cybersecurity.
The Budapest Convention on cybercrime, the first international treaty to address internet and cybercrime passed in 2004 by the Council of Europe, was modelled on the western approach. It promoted harmonising national laws with international standards of cybersecurity and cooperation between nation- states. Simultaneously the same faction promoted their agenda in the UN by forming the UN Group of Governmental Experts (GGE) for cybercrime with almost the same guidelines which were framed in the Budapest Convention.
Russia, while being a member of the GGE and an observer state on the council of Europe, had blocked any meaningful resolution from GGE and then, alongside both processes, pushed for a more independent, inclusive, transparent, and democratic body to study responsible state behaviour and cooperation in cyberspace. These efforts resulted in the OEWG (Open- Ended Working Groups) bringing about more practical approaches to ensure cooperation and development of secure cyberspace. The OEWG called for strengthening the nascent cyberinfrastructure in the developing world through the exchange of information and required equipment, an agreement among nation-states not to allow the malicious use of ICTs on their soil and an utmost emphasis on protecting healthcare and other critical sectors.
The UN finally endorsed the OEWG report in March this year, after almost a decade of talks and discussions. While it builds on the foundational understandings of the GGE reports, which emphasise an open and free internet and a need to take collective accountability for attacks that spread across national borders, it integrates other demands of the latter faction as well. The report is not legally binding and overall is not a popular endorsement for any sides. Iran went as far as to disassociate with the report stating its resolutions as unacceptable.
Assessment
- Governments should take on more proactive measures to ensure cybersecurity. There need to be more cost- benefit cybersecurity training programmes that will help private firms to invest wisely and effectively in cybersecurity.
- The government should also encourage incentives for information sharing within cooperations so that various kinds of malicious software can be effectively studied and mitigated. Most importantly, the government needs to invest heavily in R&D to counter the ever-changing nature of ransomware attacks and malicious ICTs.
- Since the private sector has the lead in most cutting-edge technology related to cyber, a private-public partnership would be most beneficial to fight the scourge of ransomware.







Comments