Lockbit : Prisoner of Conscience?
February 4, 2023 | Expert Insights

LockBit ransomware issued a formal apology after claiming responsibility for one its attacks on a Paediatric Hospital In Canada.The LockBit ransomware gang has released a free decryptor for the Hospital for Sick Children (SickKids), saying one of its members violated rules by attacking the healthcare organization.It also provided a free decryptor for and terminated the partner from their affiliate program who attacked this hospital citing violation of rules.
BACKGROUND
LockBit is one of the malwares in the world which can block users' access to its own system in exchange for a ransom payment. Formerly known as “ ABCD” software, it is considered as the fastest encryption service in the world of dark web. LockBit’s main focus is on enterprises and individuals rather than individuals .
This dangerous ransomware was first noticed in 2019 and has now upgraded themselves with newer and more efficient versions such as LockBit 3.0. LockBit’s initial focus was across countries like the USA, UK, Germany, China, India, France and Indonesia. Further it avoided countries like Russia with the fear of prosecution.This malicious software uses the Ransomware-as-a-Service (RaaS) model, wherein affiliates pay the operators to launch custom sized attacks.
What makes LockBit unique is its ability to self propagate, like a pre designed automated device.
This malware does not require any directions from anyone , they like spreading their own wings.
How does it work?
When an attacker manually infects a single host, they can find and connect other hosts to spread the infection by executing scripts designed to destroy your system. And all of this occurs without any human intervention!On the other hand it employs tools which mimic the nature of indigenous systems and goes undetected while execution.
Stages in a LockBit Attack:
- Exploit : First the attackers will exploit any weaknesses in your system
- Infiltrate : Then they will infiltrate deeper to complete the attack setup
- Deploy : And finally they will deploy the encryption payload and the ransomware begins its work
ANALYSIS
On 18th December 2022, a week before Christmas Canada’s hospital for Sick children was hit by Ransomware attack . And the hospital released a statement saying “Impacted systems may be offline for a prolonged period of time but patient care is continuing.” They also mentioned that it would take weeks before all of its systems were back up and running .
The attack affected doctors’ ability to access lab and imaging results, increasing the wait times for patients.
This incident not only captured the world’s attention but also ended on an interesting note.
Considered unusual, the LockBit ransomware group has claimed responsibility for their actions. Issued a formal apology and also provided the hospital with a free decryptor.This rare expression of regret raised quite a lot of eyebrows. Could it be that the so-called dangerous ransomware group has a heart of gold or is it just trying not to bring much of the world's attention.
But the question still lingers!
There are few explanations to this scenario.
- One of the plausible reasons would be giving them the benefit of doubt as the gang claimed that they didn't realize the target was a Children’s hospital and they would never have done so if they had known.
- It is possible that they might have maxed out their waiting time and wanted to proceed ahead with their next target.Because there is a two week gap between the attack and release of the decryptor.
- This might also be just an attempt to be in the good books in the public's eye. Cause targeting hospitals and healthcare is highly questionable as it involves a life threat scenario and would also bring in a lot of unwanted attention from authorities.
Whatever might be the reason , this incident is a reminder to all of us that the ransom payment should be avoided and doing that doesn’t guarantee demanding more ransom.
Assessment
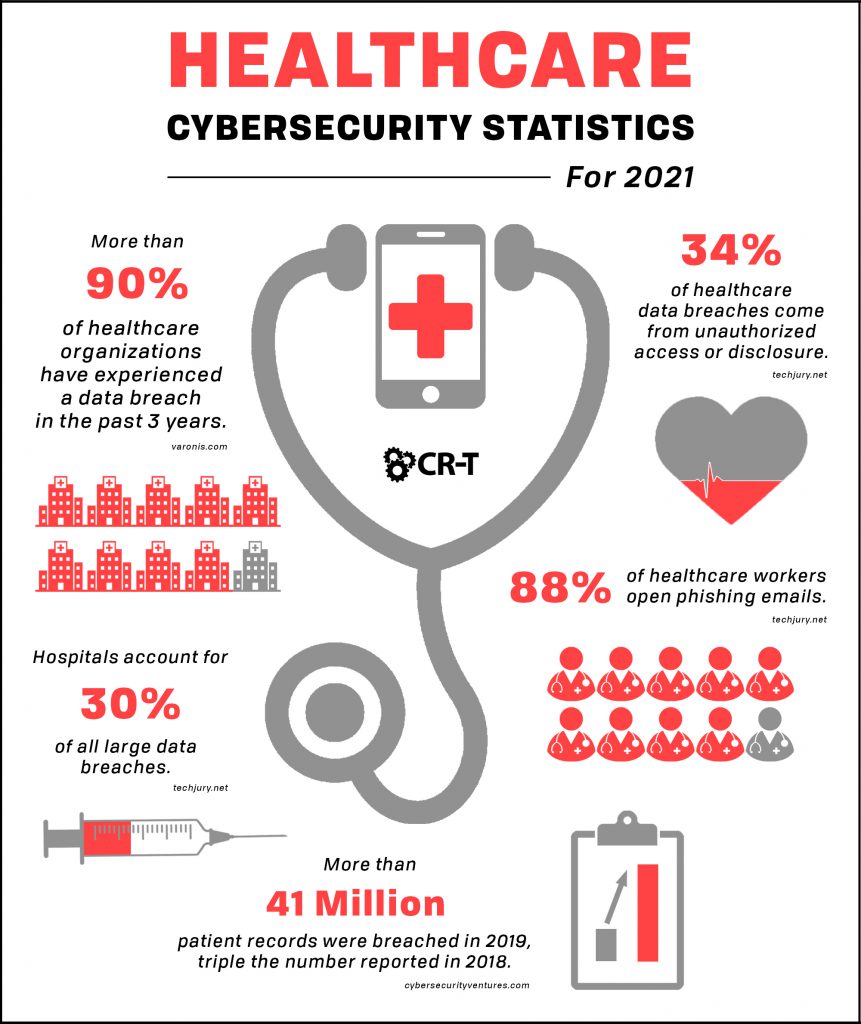
- Cyberattacks on health care systems have augmented after the pandemic considering the massive shift towards telehealth. This unprecedented turn of events have given a leverage to cyber criminals to exploit the situation
- To minimize the risk and brace themselves against a cyber attack, Hospital administration can take several precautionary measures.
- One of the options would be strengthening their network defenses. Such as providing latest updates to their antivirus and firewall systems
- And an effective education for all the employees which can make them understand the dangers and signs of a potential attack
- The other approach could be setting up a backup system in case of an attack to restore the data.
- Subsequently the laws and policies approaching cybercrimes against a healthcare system should be more aggressive at both national and international levels.








Comments