Cyber-proofing Space Assets
February 18, 2023 | Expert Insights

Investing huge sums in space assets is not simply a matter of luxury, promoting national pride or achieving hidden military objectives even for developing countries; the very future of our civilisation will increasingly depend upon this medium. Cyber-controlled physical hardware in outer space, i.e., satellites for applications such as banking, transportation, navigation, communication, weather forecasting, electricity grids, agriculture, mining, the internet and the transit of goods worldwide, will be controlled, managed and protected from space.
But space remains a vulnerable critical infrastructure. Due to the deep integration of space, cyber assets and data systems, seemingly standalone and minor disruptions, such as a targeted attack on a particular satellite, could swiftly turn to impact viral targets spread across the globe, far from the intended targets. The rise and wide adoption of the Internet of Things (IoT) are further predicted to aggravate these ripple effects, given that space systems are a crucial IoT component.
The Ukraine war provides ample proof of this. A Russian cyberattack in March 2022 on Viasat terminals allegedly targeted Ukrainian military C2 capacities, which also led to millions of civilian internet users losing connectivity. Civilian infrastructure, including commercial airline service, was affected by the hacking of Global Navigation Satellite Systems, which cater to billions across all sectors of society. On the other hand, Ukrainians have been sending drones and missiles with uncanny accuracy aiming at signals emanating from the smartphones of Russian military leadership, scoring record levels of combat deaths among Russian generals.
Background
The U.S. National Institute of Standards and Technology defines "a cyberattack via cyberspace as one that targets an enterprise by destroying or administering a computing infrastructure in a hostile manner, or by undermining the integrity of data or pilfering proprietary information." (https://csrc.nist.gov/glossary/term/Cyber_Attack#:.)
With the increasing participation of satellites in cyberspace, they are more prone to such cyber-attacks than often perceived, with intrusions capable of collecting, transmitting and controlling the datastream, as well as the data itself. While space cyber-attacks do require a high degree of cognisance about the targeted space assets, significant resources to conduct such an attack are not required.
To impair, sabotage and maliciously control satellites besides their terrestrial systems, hackers can use multifarious modi operandi such as spoofing, jamming and gaining control of satellite networking to maximise system vulnerabilities.
Such susceptibility to cyber interference is considerable, with the rising numbers of cyber-attacks against satellite systems and the achievement of space security getting complicated by the space-cyber nexus.
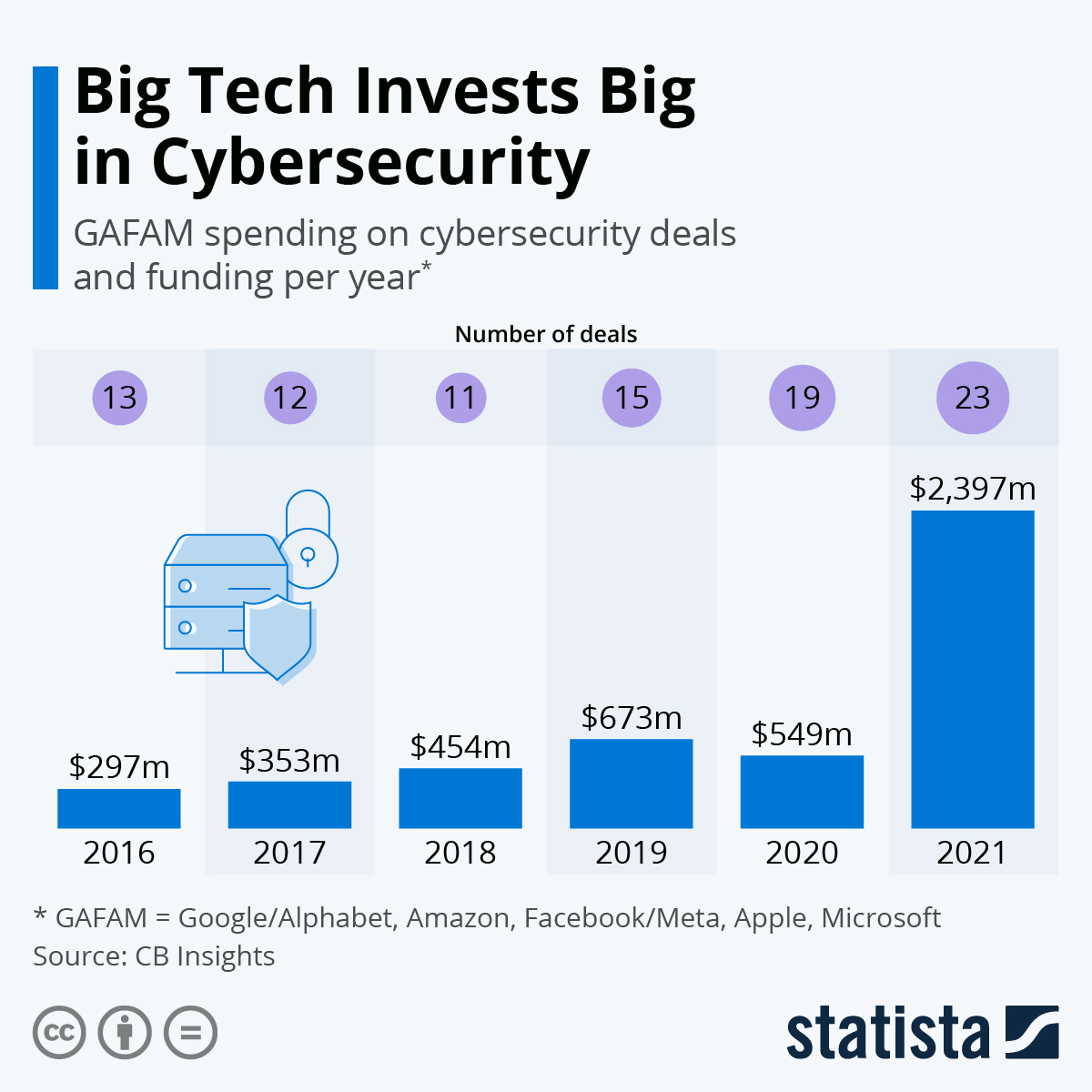
Analysis
Cyber-attacks on space assets can be distributed across an entire system or can target multiple systems simultaneously, causing large-scale disruption and even lasting damage. Nonetheless, because of the discrete nature of these attacks, they are considered less escalatory than kinetic threats to satellites.
Yet far from benign, cyberattacks can rapidly escalate to a hot war because while reluctance has been shown by nation-states to strike first kinetically, the same response hasn't been applicable to using cyber capabilities. This limitless, unregulated usage of cyber capabilities to attack adds to the dangers such threats pose.
Moreover, cyber disruption is not only difficult to distinguish from unintended or natural sources of interference to satellite systems but also hard to be attributed to specific actors because the low economic cost of such attacks enables private players, either independent or proxies of nation-states, to dangerously impact space systems. These factors render it difficult to disprove denials by perpetrators, thereby increasing the risks of misinformation, miscommunication, and misperception, which can unpredictably escalate the conflict. What adds to the threat is that for most nations, the systems for military intelligence, surveillance and command, control, and communications for early warning of missile attacks and possible nuclear threats run through space.
One of the ways in which cyber warfare can be used to harm both commercial and military satellites that blur the boundaries between kinetic and digital attacks is the taking over of satellites and turning them into projectiles to crash into other satellites. It is also possible to disable targeted satellites using such intrusions to cause secondary damage, an example of which is when the hackers, upon taking control of the German ROSAT astronomy satellite, killed it by directing its solar panels at the sun, thereby overcharging it. Additionally, the satellites which are dead because of such attacks turn into or produce debris, which continue to pose safety challenges to other objects in the same orbit.
Risks to space assets can also be earthbound, including attacks targeting ground infrastructure and computer systems that result in information theft or denial of service, which are also equally harmful.
It can be assumed that major space powers like the U.S., China and Russia would be developing the capacity to exploit cyber and space domains to further their geopolitical, geoeconomic and military objectives. Consequently, in 2019, NATO established space and cyber commands, thereby recognising space as a new operational environment. This reflects the interdependence between the two domains-space and military-with the intent of enabling a more effective response to digital crises of space assets besides enhancing defence and deterrence capacities.
This threat environment in an increasingly fragmented geopolitical environment calls for a dual track of more comprehensive governance policy approach and technological guidelines that can direct the application of defensive measures such as high-grade encryptors, intrusion, botnet, denial of service attack detection as well as antivirus and ransomware protection capabilities that can safeguard operational satellite system components both in space as well as terrestrially.
A new approach specifically designed for space systems that combine automated defensive tools and advanced risk assessment along with traditional management of threats security information will successfully increase the cost and complexity for cyber attackers, thereby enhancing space asset resiliency. The potential of quantum satellites that are theoretically resilient to the usage of the huge processing power of quantum computing in future that can be used by hackers for de-encryption of existing advanced cryptography used to protect key digital infrastructure, including space assets, is also interesting and worth further exploration.
The present international legal order is ill-equipped to curb the weaponisation of orbit environments occupied by satellites and the mutual distrust sprouting among nations regarding each other's space assets and cyber-attack capabilities, as well as trading of orbit spaces. Moreover, the unpredictability and cross-border nature of certain non-state actors are stalling efforts in this direction.
The 1967 Outer Space Treaty and International Telecommunication Union regulations are weak and do not offer adequate global protection to satellite systems, amounting to disparate protocols limited by national strategies that result in nominal international cooperation and space governance riddled with loopholes and lacunae.
A positive approach to overcome the mutual mistrust existing among major space players can be an identification of key common security interest areas such as debris removal, protection of satellite data and systems from cyber terrorists, and climate protection.
However, the development of a voluntary rules-based and liberal international order to cyber-proof space assets might be opposed by the developing states in the Global South, who, given their experiences of deprivation and limited space footprint, might treat the outcome of such an approach as discriminatory.
Assessment
- Although international treaties partly cover certain categories of kinetic attacks against space assets, digital threats to critical space infrastructure are dangerously unregulated, with the Budapest Convention being the only international treaty on cybercrimes; however, even that doesn't feature any space-specific clause and is not binding on important strategic players in outer space - Russia and India.
- Susceptibility to cyber-attacks on space assets is universal, although operational capacities to identify, mitigate and respond to such threats vary vastly across countries. This necessitates going beyond national strategies, a multilateral, flexible and democratic solution to the digital dangers facing the cyber-space nexus that is acceptable to all in terms of ensuring space safety and sustainability.
- Addressing competition and threats to the space economy can be best realised by combining and leveraging government, academia and industry roles to formulate a tailored and comprehensive space and cyber policy.








Comments