Tempering Cyber Sovereignty
August 7, 2021 | Expert Insights

At an industry event organised by the Internet and Mobile Association of India, the National Cybersecurity Coordinator - Lt. General Rajesh Pant, has remarked that the country will roll out its cybersecurity strategy later this year. According to him, ‘an element of sovereignty will be introduced to ‘create a safe, secure, resilient, trusted and vibrant cyberspace for national prosperity.
BACKGROUND
The concept of ‘sovereignty’ can be traced back to a series of peace treaties signed in 1648, following the Thirty Years’ War and the Dutch War of Independence. It had sowed the seeds for a Westphalian system of governance, wherein states were granted sovereignty over their respective territories and domestic affairs, without any intervention by other countries.
Despite its long history, however, the notion of sovereignty was not initially applied to the cyber realm. In the early days of the internet, it was considered to be impervious to state control, given its interconnected nature that defied national borders.
Over the years, however, there was a discernible spurt in the number of internet users around the world, with growing applications in social, economic, political and military domains. Nation-states were increasingly made aware of the need to exercise a degree of sovereignty or control over the virtual space. Accordingly, the United Nations Governmental Group of Experts (UNGGE) decided in 2015 that principles of International Law, including state sovereignty, would be applicable to cyberspace.
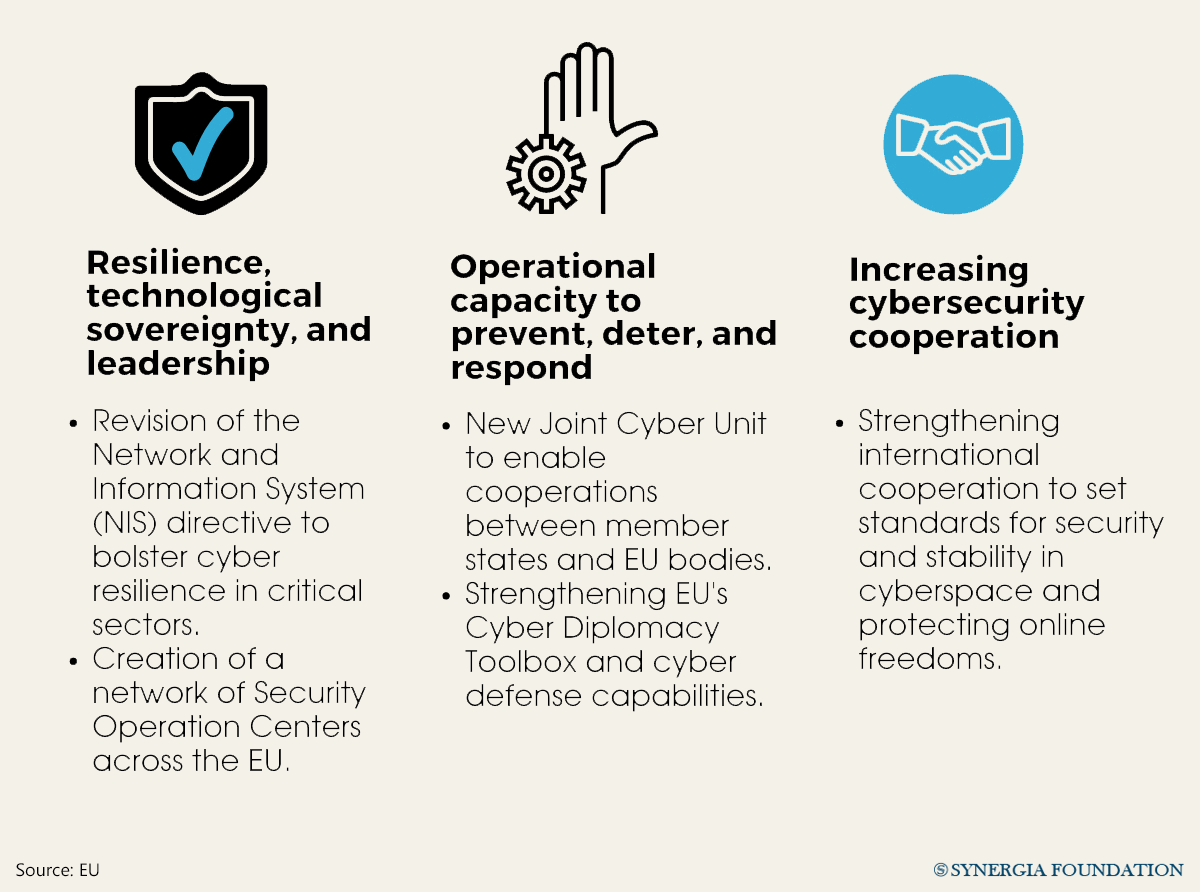
ANALYSIS
Even though cyber sovereignty has been extensively discussed in the context of international law, states disagree about the extent of control that can be exercised over the internet. On one hand, countries like the United States and its allies call for free and open cyberspace. Given that the internet continues to be dominated by Silicon Valley companies, Western ideas about privacy, free speech, and access to information are invoked to assert minimal control over internet traffic.
On the other hand, states like China and Russia espouse a cyber sovereignty model that closely monitors internet data to protect national interests. According to critics, however, this model is often exploited to tighten control over internet gateways and censor online political content. In China, for example, this has manifested in the form of the ‘Great Firewall’ that deploys a combination of legislative actions and filtering technologies to domestically regulate the Internet. Meanwhile, Russia has enacted its own ‘Sovereign Internet Law’ that seeks to censor content, localize data, survey citizens, and criminalize online activity.
In recent years, however, even the most liberal democracies have recalibrated their position on cyber sovereignty. The growing dominance of big technology firms and the unchecked flow of information are perceived as a threat to democratic values, mandating content moderation and data localisation norms.
For example, jurisdictions like Japan, the European Union and the United Kingdom have designed limits on free data flows. Similarly, India has relied on its Information Technology (IT) Act to monitor and intercept online data in the interests of national sovereignty. Its pending data protection bill also seeks to strike a balance between data sovereignty and a ‘free and fair digital economy’.
Against this backdrop, the proposal to incorporate elements of sovereignty in the upcoming national cybersecurity strategy comes as no surprise The pursuit of hybrid warfare by nation-states and non-state actors poses a significant concern for critical infrastructure in the country. With an exponential increase in cyber-crimes, especially phishing attacks and ransomware, access to data has become extremely crucial for law enforcement agencies to uphold sovereign interests.
COUNTERPOINT
Although the rationale for referencing sovereignty in the National Cybersecurity Strategy cannot be disputed, it is a slippery slope. An unrestricted collection of sensitive data by government agencies, in the garb of cyber sovereignty, can have grave implications for human rights and internet freedom. Data localisation laws may operate as a pretext for expanding censorship and surveillance powers, as was seen in the case of China.
Already, the Indian government is caught in the eye of a political storm, following allegations of snooping using Israeli spyware, Pegasus. In the past, the country has also been criticised for imposing internet shutdowns in Kashmir and restricting digital rights on the grounds of ‘state security’ In this context, India must explore mechanisms that reconcile cyber sovereignty laws with the fundamental rights of citizens.
ASSESSMENT
- In devising its national cybersecurity strategy, India must avoid a zero-sum trade-off between sovereign interests and civil liberties. It must meaningfully engage with policymakers, tech companies and civil society members, to avoid being drawn into the US-China technological bipolarity.
- By distinguishing itself from the sovereign internet models employed in China and Russia, India can potentially emerge as a global norm-setter for democratic countries.







Comments