PERILS OF DIGITAL HEALTH CARE
August 13, 2022 | Expert Insights

Digital technologies rule the medical world in providing lifesaving solutions at very affordable rates, especially for large public health services. However, the cost involved in hard casing them against cyber threats has invariably led to loosely constituted cyber security measures. It is, therefore, no surprise that an increasing number of cyber criminals are attacking these medical networks through ransomware attacks for rich pickings from an organisation that has no choice but to pay.
This is but a small glimpse of the future when society's dependence on the digital world is opening a new area for ruthless criminals, ready to paralyse a lifesaving service for the sake of money, and a great deal of it.
Background
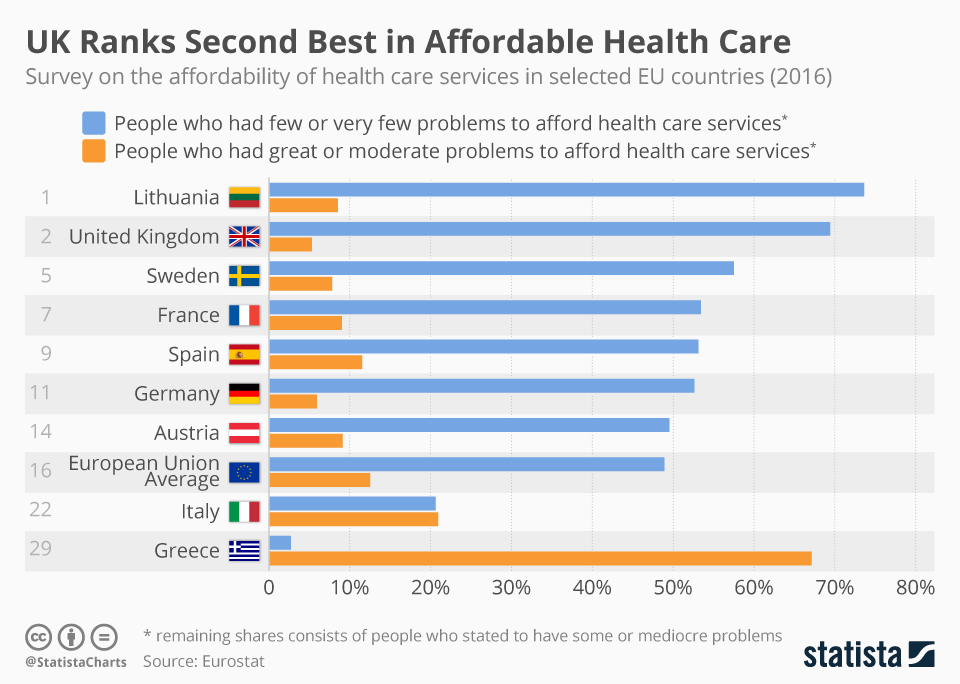
The UK's National Health Service (NHS) is one of the four national health care systems and is publicly funded. Globally it ranks only after the Brazilian Sistema Unico de Saude as the largest single-payer health care system. Its size and outreach make it extremely vulnerable. This became evident when the NHS helpline was compromised once again this month.
A British service provider, Advanced, runs this system through the Adastra platform, and a cyber-attack paralysed 85 per cent of the NHS emergency helpline on August 4th. Chaos reigned as the NHS 111 emergency helpline stopped responding to medical emergencies like cardiac arrests, strokes and even road accidents. Even routine functioning like patient referrals and prescription services were impacted throughout the UK. Private doctors had to be kept on standby to handle emergency cases like it was done in the pre-digital era. Health chiefs in the UK have warned that medics may be unable to access patient notes for three weeks, now exclusively stored digitally.
The perpetrators behind the attack are yet to be identified; however, experts believe this is likely the work of a ransomware gang. The National Crime Agency (NCA) has been working with Advanced to investigate the cyberattack. Advanced’s COO Simon Short stated that the attack was limited “to a small number of servers that made up about 2 per cent of Advanced’s health and care infrastructure”.
The attack was not unexpected because, in light of the Ukraine-Russia conflict, NHS England had sent an advisory to medical centres and trusts advising them to have their IT services patched, protected and ready with backups. Clearly, the warning was not enough.
Analysis
According to a Sophos report, ransomware attacks on the healthcare sector have increased by 94 per cent after the pandemic. Ransomware is a type of malicious software that encrypts data in a victim’s system and holds it hostage until a ransom is paid to the perpetrator. A study by Obrela Security Industries showed that 81 per cent of healthcare organisations in the UK had faced a ransomware attack in 2021. But even before the pandemic, the NHS was victim to large-scale cyberattacks such as the 2017 WannaCry ransomware attack. WannaCry disrupted the functioning of 600 primary care organisations and 81 NHS trusts and cancelled nearly 19,000 appointments leading to an estimated loss of £91 million.
Experts call notice to the low-quality security being afforded to these lifesaving networks due to the paucity of public funds for resilience building. According to a report by CyberEdge, UK firms were the fifth lowest spenders when it came to IT security in 2021. Despite the UK garnering nearly £300 million in investments since 2017 to strengthen its cybersecurity, the awareness of potential cyber threats is still low amongst health professionals.
While other critical infrastructure sectors are also subjected to such attacks, the healthcare sector presents unique challenges. In the health industry, problems can vary from malware that jeopardises system integrity and patient privacy to distributed denial-of-service (DDoS) assaults that prevent institutions from delivering care to patients. It's important to realise that cyberattacks can have effects beyond monetary loss and privacy violations; they can mean death itself if emergency medical attention is delayed or denied.
Despite multiple cyberattacks and data breaches, the NHS still fumbles when handling cybersecurity incidents. One of the main reasons for this unpreparedness comes from how cybersecurity is imbibed into an organisation. Cybersecurity must be built ground-up in every organisation to ensure complete protection from intrusions and leaks.
India, with its galloping pace of digitalisation, is in the process of creating a centralised digital health record repository for its Ayushman Bharat Digital Mission, the home-grown public health programme. In the absence of a data protection bill and outmoded IT regulations, and a credible cybersecurity ecosystem, the medical data of millions of Indians could be compromised, and the system rendered useless by ransomware attacks. India would do well to closely study the case of the UK's NHS to draw lessons and design its own digital shield.
Assessment
- Health services across the world need to be provided with the highest level of cyber security, perhaps at par with national defence and Critical Infrastructure. Also, dependence on a single vendor for emergency helpline services for such an extensive system like the NHS is highly dangerous; redundancy must be inbuilt into the network.
- Governments must proactively safeguard the healthcare industry by engaging in mandatory basic cybersecurity training and workshops for medical professionals. Ignorant employees are more likely to aid a cyberattack unintentionally, as most malicious intrusions are enabled by human error or lapses.
- To ensure that threat actors are held accountable, governments must increase the ability of law enforcement agencies and judicial systems to intervene in extraterritorial situations. Moreover, they ought to work together to guarantee that these laws are implemented to combat transnational criminal networks.







Comments