Offensive Cyber
December 19, 2017 | Expert Insights
To assure their own cybersecurity, states will sometimes intrude into the strategically important networks of other states and will threaten, often unintentionally, the security of those other states - risking escalation of mistrust, and undermining stability.
Background
A cyber threat is deemed any malicious act that attempts to gain access to a computer network without authorization or permission from the owners. In 2017, there were multiple cyber threats that manifested into large scale attack on systems worldwide. The WannaCry attack alone ended up affecting hundreds of systems across the world including hospitals and large organizations. Internet connectivity brings great benefit, but is also exploited by those wishing to cause harm.
In addition, it was revealed that financial systems like Equifax had been breached and data of millions of people became vulnerable. In November, Uber confirmed that it had been hacked and 57 million customers and drivers were affected.
Nation states also develop cyber capabilities that can be weaponized. Countries like Russia and North Korea have been linked to cyber breaches of other nations. Cyber warfare has become a legitimate force to be reckoned with as a cyber attack can destabilize important structures vital to a nation.
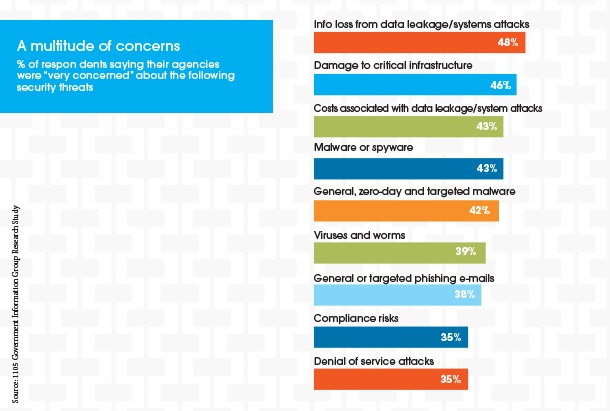
Analysis
Max Smeets, Cybersecurity Fellow, Stanford University Center for International Security & Cooperation and Frédérick Douzet, Castex - Chair of Cyber strategy, Institute of National Defense Studies, Paris spoke about ‘Offensive Cyber’ and the manner in which cyber crime can be addressed and prevented.
Frédérick Douzet said that cyber crime by itself was “systemic” and could be carried out by anybody whether it is a criminal organization or another nation state. Therefore, it is in everybody’s interest to stop it. She noted, “Mitigating these risks can require cooperation at the highest level between governments and between the public sector and the private sector. I think this approach to cyber risk is pulling us into greater international cooperation.” She pointed out that cyber operations can be seen as a tool by governments to increase their own power. She highlighted how cyber can be used as a weapon not against enemy states but allies who are economic competitors. Thus, this approach will pull nations away from international cooperation. She said that these kinds of cyber attacks have “gotten out of control” and now threaten institutions like hospitals and have created systemic risks for our societies. She noted that as long as the traditional geopolitical conflict between nations prevails, the cyber arms race will continue.
Max Smeets spoke about military cyber commands. He noted, “A growing number of states are interested in developing cyber capabilities.” He highlighted how there was still a lot of uncharted territory in the word of cyber policy or doctrine. He noted that cyber is all about “people, people and people.” He pointed out that qualified and capable people should be at the helm when creating cyber commands.

He stated that cyber weapons are often viewed as complete tools that people can simply sell or buy. He said ready-made tools won’t quite work in many situations. This should be kept in mind while building a cyber command. He also noted that the third element to a good cyber command lies in the right equipment. “For the development and the deployment of a much more advanced offensive cyber operation much more is required from an infrastructure perspective.” He said that at a minimum, a cyber command should make sure that it recruits a diverse pool of people. He said that some nations like United Kingdom have set up cyber reserve units in a bid to attract civilians with the right skills set.
Assessment
Our assessment is that even though greater cooperation may be the need of the hour when it comes to countering cyber crime, traditional geopolitical rivalries may prevent it from taking place. Hence, it is important for nation states to build the right kind of cyber command centers. We feel that countries will draw up principles to guide their militaries on what justifies deploying cyber attack weapons more broadly. There is definitely a change in the mindset that computers, just like aircrafts and ships, have offensive capability. It would be more prudent to down an enemy power plant through a cyber attack than air strike that could cause civilian causalities.








Comments