Disruptive Tech & Cyber-attack
February 24, 2023 | Expert Insights

Nation-states and malicious cyber actors' use of disruptive technologies have become a bigger worry in recent years. As technology keeps getting better, so do the tools available to people who want to hurt or bother other people. From hacking into critical infrastructure to spreading false information and propaganda, these actions could have big effects. One of the most important problems with disruptive technologies is that cyberattacks are getting more and more complicated. As more and more of our lives move online, there are more and more ways for bad people to take advantage of weaknesses in our digital systems. This can be done in many ways, such as by stealing personal information and financial data or by attacking important infrastructure like power grids and transportation systems. In this article, we will delve into instances of these attacks and look at strategies used by different countries to prevent them.
Background
Several state-backed groups are behind some of the most well-known cyberattacks in the past few years. Some of these are the APT28 group from Russia, the Lazarus group from North Korea, and the APT10 group from China. These groups are thought to be behind attacks on everything from the US presidential election to the WannaCry ransomware attack, which affected hundreds of thousands of computers around the world. Another problem is when disruptive technologies are used for propaganda or to spread false information. With the rise of social media, it is now easier than ever to tell a lot of people things that aren't true or aren't what they seem. Several groups, both state-backed and not, have used this to create division and chaos in societies all over the world. One of the most well-known examples of this is the idea that Russia tried to influence the 2016 US presidential election. US intelligence agencies say that Russian agents used many different methods, such as social media bots and spreading fake news stories, to help Donald Trump win the election.
Advanced persistent threat (APT) groups, primarily associated with nation-states, are increasingly targeting organizations outside of the government or critical infrastructure sectors. Between 2017 and 2021, the number of important nation-state incidents doubled, and Russian nation-state actors were the most successful, with a 32% success rate in 2021. While 21% of nation-state attacks targeted consumers, 79% targeted enterprises. Russia was responsible for the majority of nation-state attacks in the previous year. The preferred weapon of these threat actors is ransomware, and the "big 4" sponsors of APTs are Russia, China, North Korea, and Iran. A vast majority of organizations—about 86%—believe they have been targeted by a nation-state threat actor, and the average cost of a nation-state-backed cyberattack is estimated to be $1.6 million per incident.
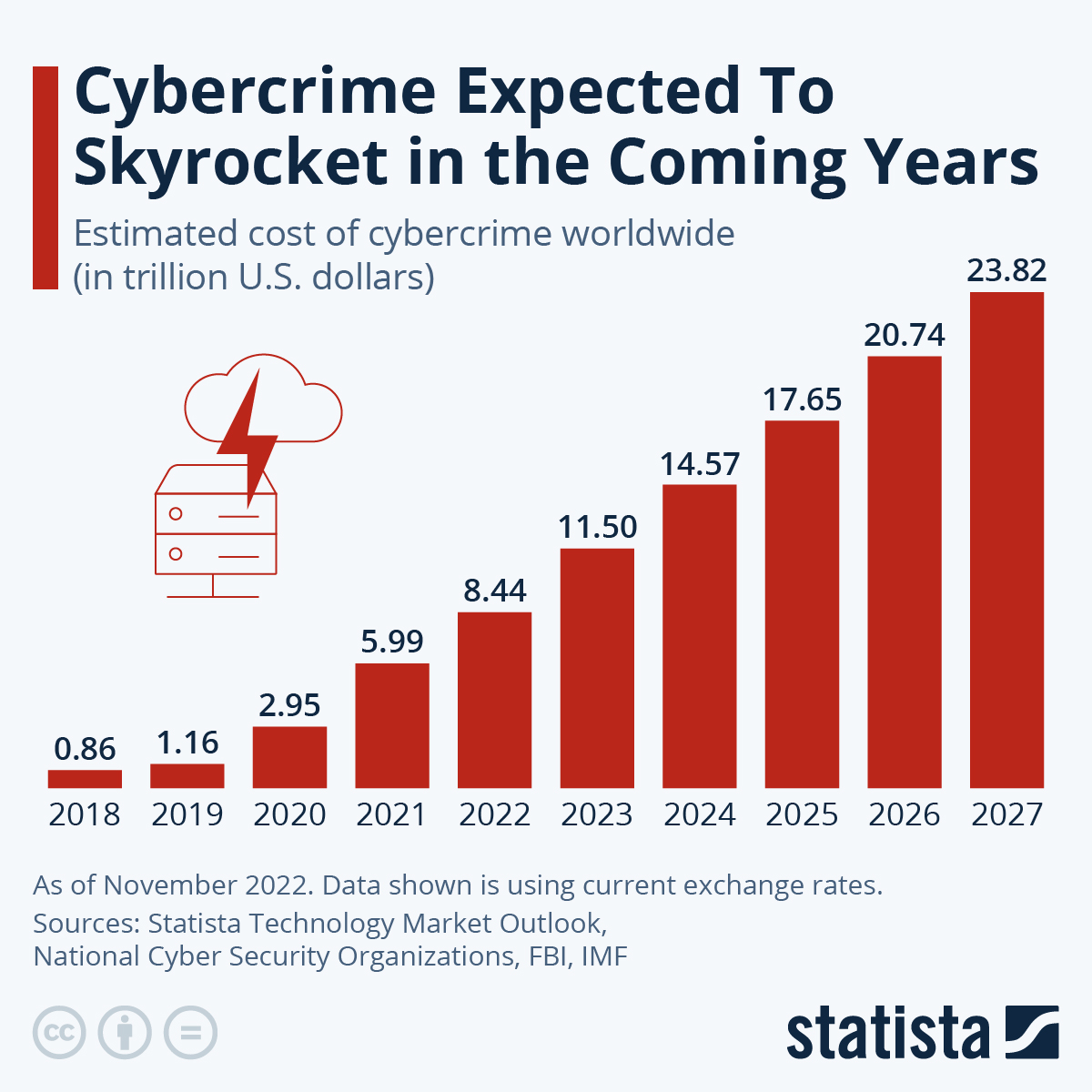
But state-backed actors are not the only ones who can use disruptive technologies. A growing number of non-state actors, like cybercriminals and hacktivists, are also using these tools for their purposes. Cybercrime is thought to cost the world economy hundreds of billions of dollars every year. Credit card fraud and ransomware attacks are just two ways that cyber criminals make illegal money. When it comes to making autonomous weapons systems, another thing that worries people is the use of technologies that change the way things work. These systems, which can work without direct human supervision, could change the way wars are fought in important ways. There are benefits to using these kinds of systems, like lowering the risk to human soldiers, but there are also some ethical questions that need to be answered.
One of the biggest problems with self-driving weapons is that they could be used in ways that break international law. For instance, there are worries that these kinds of systems could be used to kill specific people without proper oversight or accountability. There is also a chance that they could be hacked or broken in some other way, which could lead to unintended results. Because of these worries, several countries have called for a ban on weapons systems that can fight on their own. For example, the Campaign to Stop Killer Robots is a group of non-governmental organizations (NGOs) that is working to get such a ban passed. Even though progress has been slow, more and more people agree that this is a problem that needs to be fixed as soon as possible.
Prevention strategies
The growing danger of cyberattacks and the need for businesses to create strong security plans It is stressed that cyber threats have changed and become more complex, with attackers using advanced methods like artificial intelligence and machine learning. Organizations need to use a multi-layered approach to protect themselves from cyber threats. This includes giving employees regular training, putting in place strong access controls, and doing regular vulnerability assessments. Government, business, and universities need to work together more to fill the skills gap in cybersecurity and come up with new ways to protect data. It also asks policymakers to help organizations improve their cybersecurity by giving them the tools and support they need.
A national cybersecurity strategy is the most important preventive action. This strategy must identify key assets and infrastructure and describe how to protect them. The policy must be able to adapt to changes in cybersecurity and involve international cooperation to stop attacks that come from other countries. Investing in cybersecurity technologies and infrastructure is essential. This includes buying advanced security software, firewalls, intrusion detection systems, and secure networks. It's also important to set up cyber defense groups and teach cybersecurity experts how to find and deal with new cyber threats. Cybersecurity laws and regulations are another precaution. This law should define cybersecurity's legal and ethical boundaries and protect key infrastructure. It should also set sanctions for cybercrime, especially for nation-state cyberattacks.
Every government department and agency must contribute to cyber defense. To detect and minimize cybersecurity risks, this strategy incorporates risk management and vulnerability assessments. It also involves teaching employees how to avoid cyberattacks like phishing and social engineering. Preventing nation-state cyberattacks requires international cooperation. Threat intelligence, cybersecurity standards, and cybersecurity regulations must be shared by nations. This includes creating international treaties on cyberwarfare and victim treatment. Nation-state cyberattacks endanger national security and critical infrastructure. To avoid these risks, we need a national cybersecurity strategy, investments in cybersecurity technology and infrastructure, laws and rules, an approach that includes the whole government, and international cooperation. These strategies can help nation-states defend their populations and key infrastructure against cyberattacks.
In conclusion, nation-states and malicious cyber actors using disruptive technologies are a growing worry that needs to be addressed. From hacking into critical infrastructure to spreading false information and propaganda, these actions could have big effects. It's up to governments, civil society groups, and people to work together to solve these problems and make sure that technology is used for everyone's good and not to hurt or upset anyone.
Strategies adopted by nation states to mitigate these threats
- The United States has established a variety of measures to bolster its cybersecurity posture. For example, the Department of Homeland Security (DHS) has established the National Cybersecurity and Communications Integration Center (NCCIC) to offer situational awareness and analysis of cyber threats 24 hours a day, seven days a week. The US Cyber Command was also established to defend the nation's key infrastructure and military systems against cyber attacks.
- The UK has established the National Cyber Security Centre (NCSC) to give advise and assistance to government departments and providers of vital infrastructure. It has also developed the Cyber First project to teach young people in cybersecurity and cultivate the next generation of cybersecurity specialists.
- Israel has a sophisticated cybersecurity plan that includes investments in cybersecurity technologies, the establishment of a national cybersecurity authority, and the building of a cybersecurity ecosystem that promotes companies and innovators. Also, the nation is recognised for its proactive approach to cyber protection, which includes the employment of offensive cyber operations to discourage potential attackers.
- Russia has been accused of launching multiple cyberattacks against other nations, but it has also taken steps to safeguard its own key infrastructure. For instance, it has formed the Federal Service for Technical and Export Control (FSTEC) to oversee government systems and vital infrastructure in terms of cybersecurity. Also, the nation has developed its own cybersecurity goods and solutions, including as the antivirus programme Kaspersky.
- China's Cybersecurity Law controls the protection of important information infrastructure and establishes penalties for cyber offences. The country has also spent extensively in building its cybersecurity industry, including the formation of the National Cybersecurity Industrial Park and the development of its own cybersecurity products and solutions.







Comments