The Concentration Conundrum
June 23, 2021 | Expert Insights

As organisations around the world create and capture more data, there are increasing demands to employ resources provisioned over the Internet. In this veritable milieu, cloud computing has emerged as an attractive solution that facilitates a scalable online environment by offering powerful processing and storage resources. Its optimisation of infrastructure usage has reduced dependence on legacy software and ‘on premises’ alternatives, thereby lowering capital costs and operational expenses for businesses.
The responsibility for undertaking maintenance and updates has been shifted to the cloud service provider (CSP), with indirect overheads like power consumption by ‘on-premises’ hardware being eliminated. Rather than maintaining proprietary servers, enterprises can rent additional server space for a few hours at a time. This flexibility and economy of scale have been particularly expedient for small and medium-sized organisations, which lack the capacity to undertake massive investments in IT infrastructure.
Moreover, the purported agility and resilience of this networked technology has accelerated the outsourcing of computer systems to cloud-based companies’. At a time when the Covid-19 pandemic has rendered remote working a norm, the cloud has afforded employees the necessary tools to operate outside a quintessential office environment.
IMPLICATIONS FOR CRITICAL INFRASTRUCTURE
Given the unique benefits of the cloud, many critical infrastructure providers are also contemplating the migration of their workloads. Cloud computing can potentially upgrade the IT infrastructure of governments and bureaucracies, which are particularly notorious for their inefficient services and delayed response times.
The scalable platforms of cloud-based companies are also useful for vital sectors like power distribution networks that handle large amounts of data computation and multi- tenant billing. Even the financial services industry is projected to be transformed by cloud computing in the next five years. Against this backdrop, it is increasingly important to configure and manage security postures.
The cloud is susceptible to malware infections, data breaches, identity theft and other social engineering tactics, just like any other aspects of cyberspace. There are, however, other pressing concerns that need to be addressed in the short term, namely the risks posed by a concentration of CSPs.
MARKET DOMINANCE
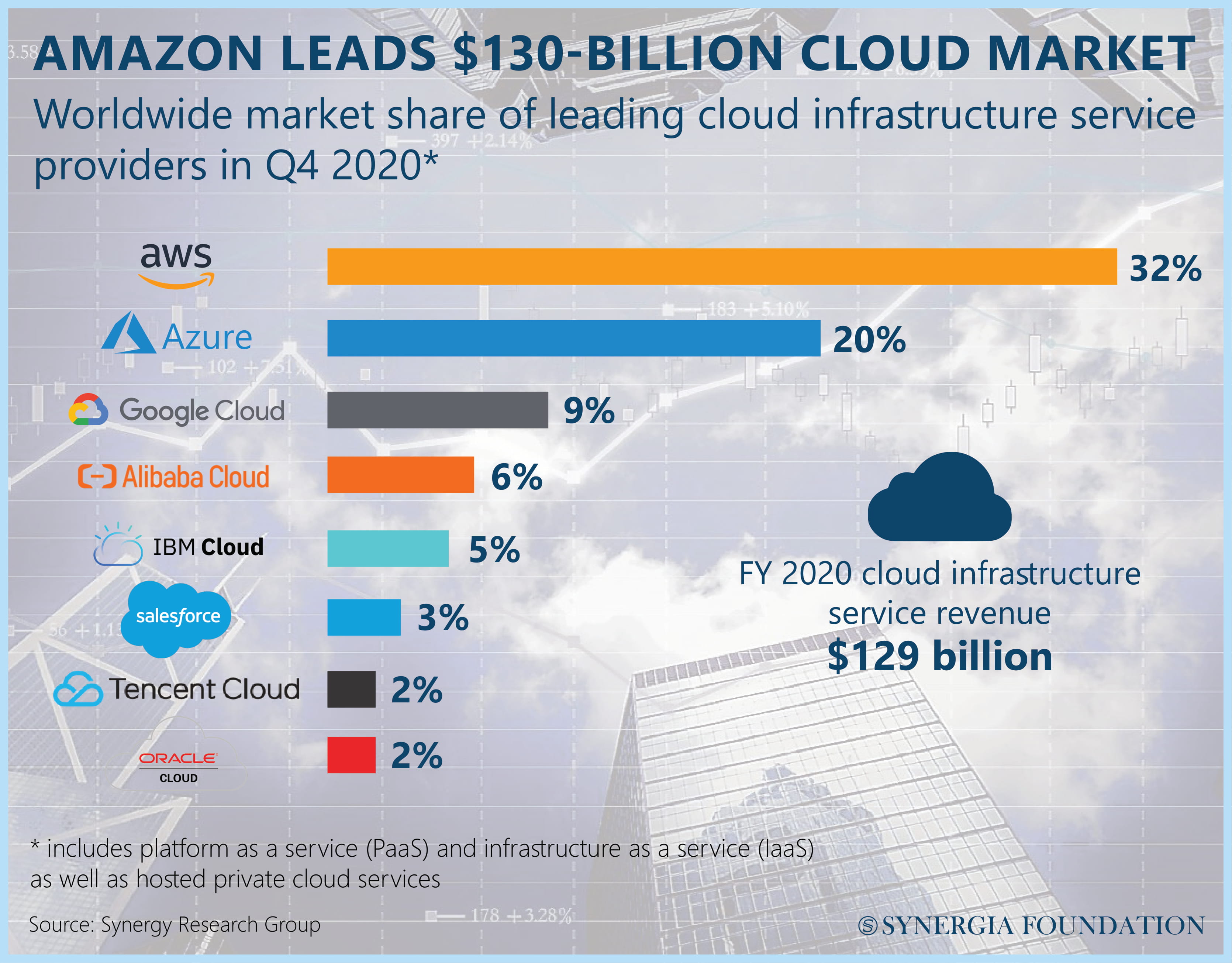
As the demand for cloud services accelerates at a rapid pace, especially in the aftermath of the Covid-19 pandemic, the markets have become more concentrated in a few key players. In 2020, it was estimated that Amazon, Microsoft, and Google accounted for nearly 71 per cent of the suppliers that offered cloud infrastructure and platforms as services. In other words, the virtual computing systems of most businesses are predicated on a few CSPs.
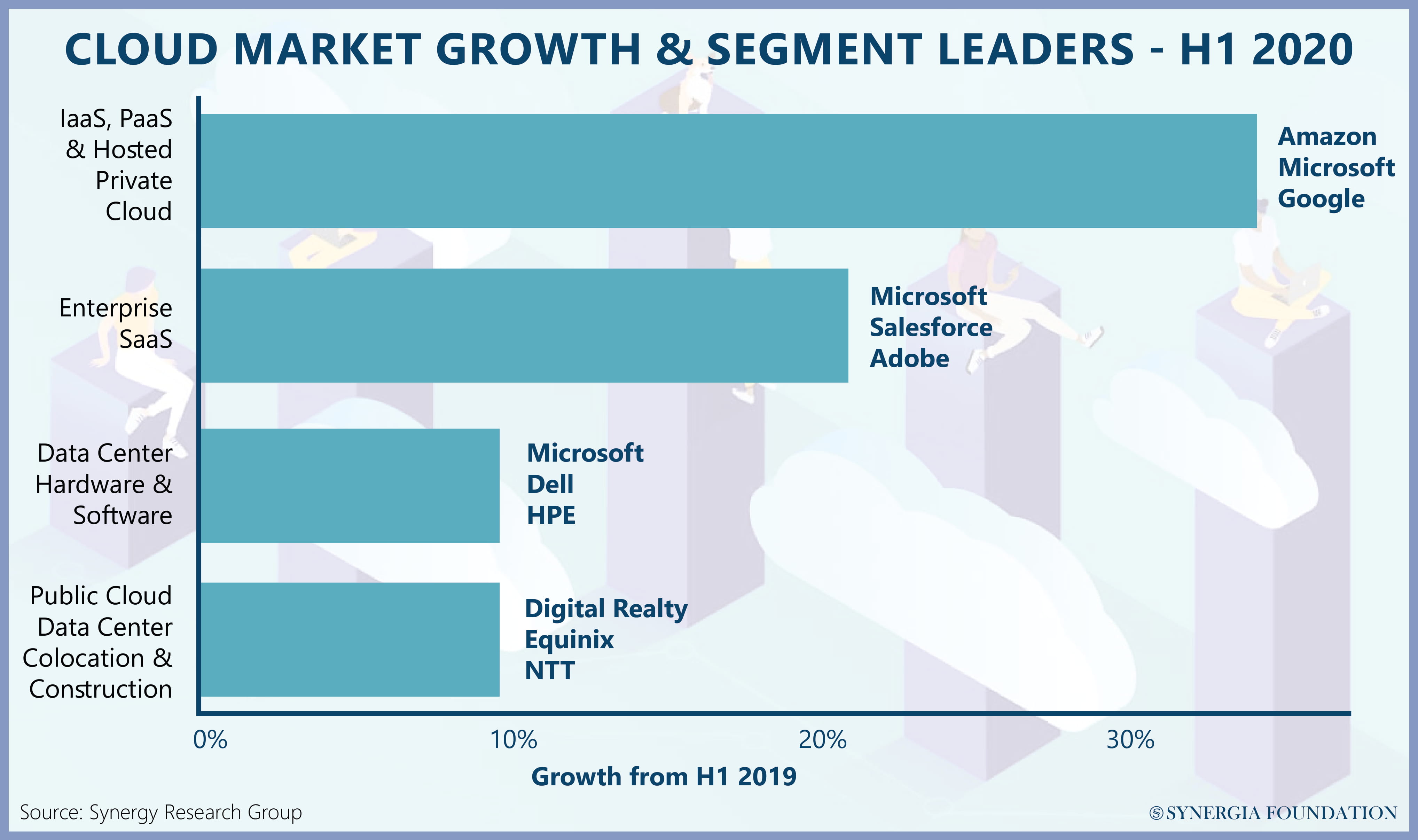
By heavily investing in security, maintenance as well as data centres around the world, these tech giants have secured the trust of their consumers in a manner that other CSPs struggle to compete with. Apart from possessing the processing power required for advanced analytics, they are often perceived to be superior in managing cybersecurity and technical risk mitigations. This historical path dependence has been supplemented by the network effect among users, which has effectively created an oligopoly of sorts in the cloud services industry.
RISKS OF CONCENTRATION
Of course, such concentration of market power can have its own advantages. Apart from benefiting from operational and cost efficiencies, CSPs can leverage their technical sophistication, skilled personnel, and security protocols to offer better services for their consumers. There are, however, other risks that accompany this unique combination of ubiquity and concentration.
When a single technology vendor has a large concentration of customers relying on its services, a single breach or outage can have a cascading effect. The 2017 server outage of Amazon Web Services, which disrupted a whole range of websites like Quora, Imgur, Trello, Flickr, Glassdoor and the Washington Post, is a case in point. More recently, incidents like the SolarWinds hack have demonstrated how the compromise of multi-client providers can affect all downstream client-customers.
Given that most software companies build their products on top of a larger cloud service provider, they are particularly exposed to such supply chain attacks. Secondly, risks are also high when a single company depends on the same cloud provider for all its mission-critical tasks. In the absence of a diversified vendor portfolio, organisations can go out of business if their lone supplier is compromised or hacked. In fact, this single point of failure makes them attractive targets for numerous threat actors. While the threshold for hacking the cloud platforms of tech giants may be high, if successful, the payoff is equally rewarding.
Finally, the dominance of a few CSPs may lead to uncompetitive pricing. Owing to their proprietary technical features and market infrastructure capability, they can effectively lock in consumers, significantly impeding the latter’s ability to negotiate favourable prices. Unless this power asymmetry between providers and consumers of cloud services is addressed, small-scale businesses may be disincentivised from migrating to secure cloud platforms.
Assessment
- To reduce risks, users of cloud services should aim to diversify their cloud portfolios if the technical environment is conducive. The entire supply chain should be scrutinised to ensure that all providers involved in data processing are complying with minimum security standards. Contingency plans should also be put in place to protect and retrieve data stored on cloud systems.
- Meanwhile, governments can assist in the mapping of concentration risks by undertaking initials surveys of CSPs, sub-contractors and services provided under cloud models. This can help to identify ‘single point’ vulnerabilities that destabilise entire systems, processes, and critical sectors.
- Policymakers should consider mechanisms that foster technological innovation and promote healthy competition in the cloud-based environment without compromising security standards. In fact, jurisdictions like the EU have already pledged €10bn for building their own cloud infrastructure as an alternative to U.S.-based providers.
Mary Kavita Dominic, is a Policy Research Associate with the Synergia Foundation. She has completed her masters in law (BCL) and South Asian Studies (MSc.) from the University of Oxford.








Comments